* Updated the utils/run_exercise.py to allow exercises to customize host configuration from the topology.json file. Now hosts and `ping` each other in the basic exercise. Other Linux utilities should work as well (e.g. iperf). ``` mininet> h1 ping h2 PING 10.0.2.2 (10.0.2.2) 56(84) bytes of data. 64 bytes from 10.0.2.2: icmp_seq=1 ttl=62 time=3.11 ms 64 bytes from 10.0.2.2: icmp_seq=2 ttl=62 time=2.34 ms 64 bytes from 10.0.2.2: icmp_seq=3 ttl=62 time=2.15 ms ^C --- 10.0.2.2 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 2.153/2.540/3.118/0.416 ms mininet> pingall *** Ping: testing ping reachability h1 -> h2 h3 h2 -> h1 h3 h3 -> h1 h2 *** Results: 0% dropped (6/6 received) ``` Only updated basic exercise, still need to update other exercises. Also, updated the root-bootstrap.sh because I was running into issues with latest version of vagrant. * Accidentially added the solution to the basic exercise in the previous commit. Undoing that here ... * Updated the topology.json file and table entries for the basic_tunnel exercise. * Updated P4Runtime exercise with new topology and table entries. * Fixed MAC addresses in P4Runtime exercise. It is working now. * Fixed MAC addresses in P4Runtime exercise starter code * Updated ECN exercise to use new topology.json file. Updated the table entries / MAC addresses as well. * Updated the topology.json file and table entries for the MRI exercise. * Updated source_routing exercise with new topology file and verified correct functionality. * Updated load_balance exercise with new topology. * Moved basic exercise triangle topology into a separate folder * Added new topology for the basic exercise: a single pod of a fat-tree. * Updated Makefiles and run_exercise.py to allow exercises to configure each switch with a different P4 program. This is mainly for the firewall exercise. * Updated Makefiles of project to work with new utils/Makefile * Updated load_balance and p4runtime exercise Makefiles * Initial commit of the firewall exercise, which is a simple stateful firewall that uses a bloom filter. Need to update README files * Initial commit of the path_monitor exercise. It is working but still need to update the README and figure out what we want the tutorial attendees to implement. * Updated README file in firewall exercise. Also removed the bits from the starter code that we want the tutorial attendees to implement * Renamed path_monitor exercise to link_monitor * Updated the README in the link_monitor exercise and removed the bits from the starter code that we want the tutorial attendees to implement. * Updated README for the firewall exercise * Adding pod-topo.png image to basic exercise * Added firewall-topo.png image to firewall exercise * Added link-monitor-topo.png to link_monitor exercise * Updated README files to point to topology images * Updated top-level README to point to new exercises. * Fixed link for VM dependencies script in README * Updated bmv2/pi/p4c commits * Updated README files for exercises to fix some typos and added a note about the V1Model architecture. * Added a note about food for thought in the link_monitor README * Updated the firewall.p4 program to use two register arrays rather than a single one. This is to make the design more portable to high line rate devices which can only support a single access to each register array. * Minor fix to firewall exercise to get rid of compiler warning. * Updated comment in firewall exercise. * Minor (typo) fixes in the firewall ReadMe * More info in firewall exercise ReadMe step 2 * Updated firewall.p4 to reuse direction variable * More testing steps, small fixes in firewall exercise Readme * Added food for thought to firewall Readme * Cosmetic fixes to firewall ReadMe * Made a few updates to the basic exercise README and added more details to the link_monitor exercise README. Also added a command to install grip when provisioning the VM. This could be useful for rendering the markdown README files offline. * Updated top level README so it can be merged into the master branch. * Moved cmd to install grip from root-bootstrap to user-bootstrap
Implementing a Control Plane using P4Runtime
Introduction
In this exercise, we will be using P4Runtime to send flow entries to the
switch instead of using the switch's CLI. We will be building on the same P4
program that you used in the basic_tunnel exercise. The
P4 program has been renamed to advanced_tunnel.p4 and has been augmented
with two counters (ingressTunnelCounter, egressTunnelCounter) and
two new actions (myTunnel_ingress, myTunnel_egress).
You will use the starter program, mycontroller.py, and a few helper
libraries in the p4runtime_lib directory to create the table entries
necessary to tunnel traffic between host 1 and 2.
Spoiler alert: There is a reference solution in the
solutionsub-directory. Feel free to compare your implementation to the reference.
Step 1: Run the (incomplete) starter code
The starter code for this assignment is in a file called mycontroller.py,
and it will install only some of the rules that you need to tunnel traffic between
two hosts.
Let's first compile the new P4 program, start the network, use mycontroller.py
to install a few rules, and look at the ingressTunnelCounter to see that things
are working as expected.
-
In your shell, run:
makeThis will:
- compile
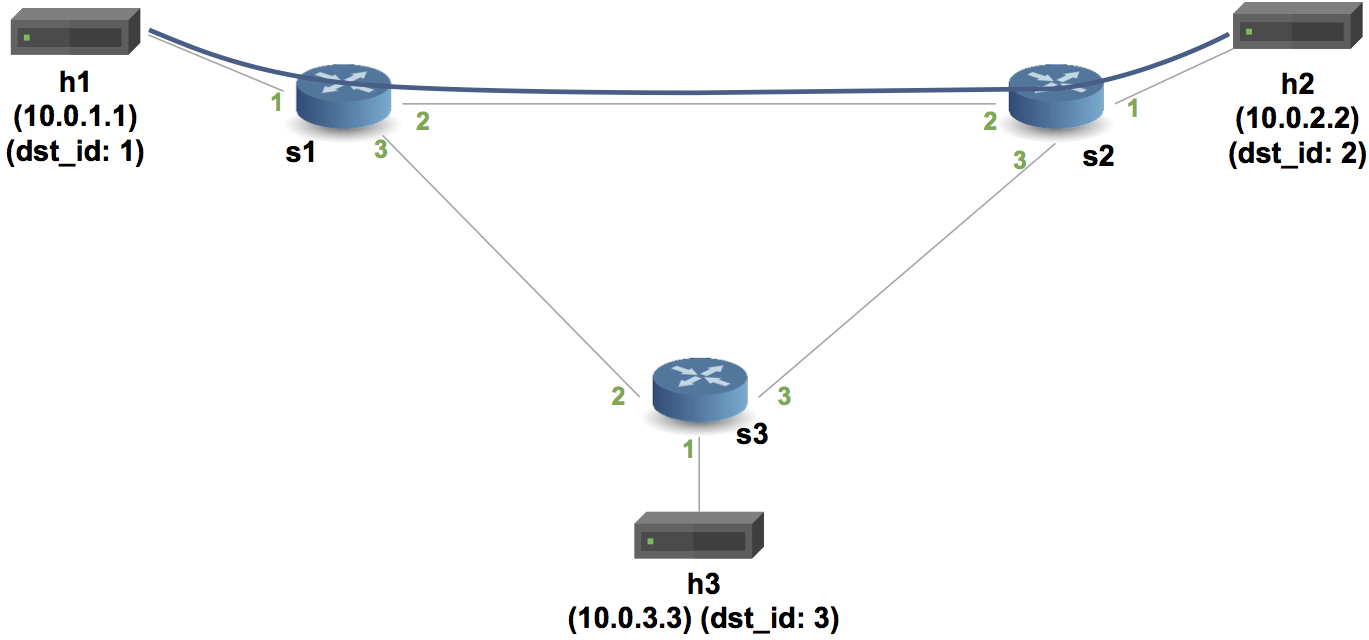
advanced_tunnel.p4, - start a Mininet instance with three switches (
s1,s2,s3) configured in a triangle, each connected to one host (h1,h2,h3), and - assign IPs of
10.0.1.1,10.0.2.2,10.0.3.3to the respective hosts.
- compile
-
You should now see a Mininet command prompt. Start a ping between h1 and h2:
mininet> h1 ping h2Because there are no rules on the switches, you should not receive any replies yet. You should leave the ping running in this shell.
-
Open another shell and run the starter code:
cd ~/tutorials/exercises/p4runtime ./mycontroller.pyThis will install the
advanced_tunnel.p4program on the switches and push the tunnel ingress rules. The program prints the tunnel ingress and egress counters every 2 seconds. You should see the ingress tunnel counter for s1 increasing:s1 ingressTunnelCounter 100: 2 packetsThe other counters should remain at zero.
-
Press
Ctrl-Cto the second shell to stopmycontroller.py
Each switch is currently mapping traffic into tunnels based on the destination IP address. Your job is to write the rules that forward the traffic between the switches based on the tunnel ID.
Potential Issues
If you see the following error message when running mycontroller.py, then
the gRPC server is not running on one or more switches.
p4@p4:~/tutorials/exercises/p4runtime$ ./mycontroller.py
...
grpc._channel._Rendezvous: <_Rendezvous of RPC that terminated with (StatusCode.UNAVAILABLE, Connect Failed)>
You can check to see which of gRPC ports are listening on the machine by running:
sudo netstat -lpnt
The easiest solution is to enter Ctrl-D or exit in the mininet> prompt,
and re-run make.
A note about the control plane
A P4 program defines a packet-processing pipeline, but the rules
within each table are inserted by the control plane. In this case,
mycontroller.py implements our control plane, instead of installing static
table entries like we have in the previous exercises.
Important: A P4 program also defines the interface between the
switch pipeline and control plane. This interface is defined in the
advanced_tunnel.p4info file. The table entries that you build in mycontroller.py
refer to specific tables, keys, and actions by name, and we use a P4Info helper
to convert the names into the IDs that are required for P4Runtime. Any changes
in the P4 program that add or rename tables, keys, or actions will need to be
reflected in your table entries.
Step 2: Implement Tunnel Forwarding
The mycontroller.py file is a basic controller plane that does the following:
- Establishes a gRPC connection to the switches for the P4Runtime service.
- Pushes the P4 program to each switch.
- Writes tunnel ingress and tunnel egress rules for two tunnels between h1 and h2.
- Reads tunnel ingress and egress counters every 2 seconds.
It also contains comments marked with TODO which indicate the functionality
that you need to implement.
Your job will be to write the tunnel transit rule in the writeTunnelRules function
that will match on tunnel ID and forward packets to the next hop.
In this exercise, you will be interacting with some of the classes and methods in
the p4runtime_lib directory. Here is a summary of each of the files in the directory:
helper.py- Contains the
P4InfoHelperclass which is used to parse thep4infofiles. - Provides translation methods from entity name to and from ID number.
- Builds P4 program-dependent sections of P4Runtime table entries.
- Contains the
switch.py- Contains the
SwitchConnectionclass which grabs the gRPC client stub, and establishes connections to the switches. - Provides helper methods that construct the P4Runtime protocol buffer messages and makes the P4Runtime gRPC service calls.
- Contains the
bmv2.py- Contains
Bmv2SwitchConnectionwhich extendsSwitchConnectionsand provides the BMv2-specific device payload to load the P4 program.
- Contains
convert.py- Provides convenience methods to encode and decode from friendly strings and numbers to the byte strings required for the protocol buffer messages.
- Used by
helper.py
Step 3: Run your solution
Follow the instructions from Step 1. If your Mininet network is still running, you will just need to run the following in your second shell:
./my_controller.py
You should start to see ICMP replies in your Mininet prompt, and you should start to see the values for all counters start to increment.
Extra Credit and Food for Thought
You might notice that the rules that are printed by mycontroller.py contain the entity
IDs rather than the table names. You can use the P4Info helper to translate these IDs
into entry names.
Also, you may want to think about the following:
-
What assumptions about the topology are baked into your implementation? How would you need to change it for a more realistic network?
-
Why are the byte counters different between the ingress and egress counters?
-
What is the TTL in the ICMP replies? Why is it the value that it is? Hint: The default TTL is 64 for packets sent by the hosts.
If you are interested, you can find the protocol buffer and gRPC definitions here:
Cleaning up Mininet
If the Mininet shell crashes, it may leave a Mininet instance running in the background. Use the following command to clean up:
make clean
Running the reference solution
To run the reference solution, you should run the following command from the
~/tutorials/P4D2_2017_Fall/exercises/p4runtime directory:
solution/my_controller.py
Next Steps
Congratulations, your implementation works! Move onto the next assignment mri!