* Updated the utils/run_exercise.py to allow exercises to customize host configuration from the topology.json file. Now hosts and `ping` each other in the basic exercise. Other Linux utilities should work as well (e.g. iperf). ``` mininet> h1 ping h2 PING 10.0.2.2 (10.0.2.2) 56(84) bytes of data. 64 bytes from 10.0.2.2: icmp_seq=1 ttl=62 time=3.11 ms 64 bytes from 10.0.2.2: icmp_seq=2 ttl=62 time=2.34 ms 64 bytes from 10.0.2.2: icmp_seq=3 ttl=62 time=2.15 ms ^C --- 10.0.2.2 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 2.153/2.540/3.118/0.416 ms mininet> pingall *** Ping: testing ping reachability h1 -> h2 h3 h2 -> h1 h3 h3 -> h1 h2 *** Results: 0% dropped (6/6 received) ``` Only updated basic exercise, still need to update other exercises. Also, updated the root-bootstrap.sh because I was running into issues with latest version of vagrant. * Accidentially added the solution to the basic exercise in the previous commit. Undoing that here ... * Updated the topology.json file and table entries for the basic_tunnel exercise. * Updated P4Runtime exercise with new topology and table entries. * Fixed MAC addresses in P4Runtime exercise. It is working now. * Fixed MAC addresses in P4Runtime exercise starter code * Updated ECN exercise to use new topology.json file. Updated the table entries / MAC addresses as well. * Updated the topology.json file and table entries for the MRI exercise. * Updated source_routing exercise with new topology file and verified correct functionality. * Updated load_balance exercise with new topology. * Moved basic exercise triangle topology into a separate folder * Added new topology for the basic exercise: a single pod of a fat-tree. * Updated Makefiles and run_exercise.py to allow exercises to configure each switch with a different P4 program. This is mainly for the firewall exercise. * Updated Makefiles of project to work with new utils/Makefile * Updated load_balance and p4runtime exercise Makefiles * Initial commit of the firewall exercise, which is a simple stateful firewall that uses a bloom filter. Need to update README files * Initial commit of the path_monitor exercise. It is working but still need to update the README and figure out what we want the tutorial attendees to implement. * Updated README file in firewall exercise. Also removed the bits from the starter code that we want the tutorial attendees to implement * Renamed path_monitor exercise to link_monitor * Updated the README in the link_monitor exercise and removed the bits from the starter code that we want the tutorial attendees to implement. * Updated README for the firewall exercise * Adding pod-topo.png image to basic exercise * Added firewall-topo.png image to firewall exercise * Added link-monitor-topo.png to link_monitor exercise * Updated README files to point to topology images * Updated top-level README to point to new exercises. * Fixed link for VM dependencies script in README * Updated bmv2/pi/p4c commits * Updated README files for exercises to fix some typos and added a note about the V1Model architecture. * Added a note about food for thought in the link_monitor README * Updated the firewall.p4 program to use two register arrays rather than a single one. This is to make the design more portable to high line rate devices which can only support a single access to each register array. * Minor fix to firewall exercise to get rid of compiler warning. * Updated comment in firewall exercise. * Minor (typo) fixes in the firewall ReadMe * More info in firewall exercise ReadMe step 2 * Updated firewall.p4 to reuse direction variable * More testing steps, small fixes in firewall exercise Readme * Added food for thought to firewall Readme * Cosmetic fixes to firewall ReadMe * Made a few updates to the basic exercise README and added more details to the link_monitor exercise README. Also added a command to install grip when provisioning the VM. This could be useful for rendering the markdown README files offline. * Updated top level README so it can be merged into the master branch. * Moved cmd to install grip from root-bootstrap to user-bootstrap
Implementing ECN
Introduction
The objective of this tutorial is to extend basic L3 forwarding with an implementation of Explicit Congestion Notification (ECN).
ECN allows end-to-end notification of network congestion without
dropping packets. If an end-host supports ECN, it puts the value of 1
or 2 in the ipv4.ecn field. For such packets, each switch may
change the value to 3 if the queue size is larger than a threshold.
The receiver copies the value to sender, and the sender can lower the
rate.
As before, we have already defined the control plane rules for routing, so you only need to implement the data plane logic of your P4 program.
Spoiler alert: There is a reference solution in the
solutionsub-directory. Feel free to compare your implementation to the reference.
Step 1: Run the (incomplete) starter code
The directory with this README also contains a skeleton P4 program,
ecn.p4, which initially implements L3 forwarding. Your job (in the
next step) will be to extend it to properly append set the ECN bits
Before that, let's compile the incomplete ecn.p4 and bring up a
network in Mininet to test its behavior.
-
In your shell, run:
makeThis will:
- compile
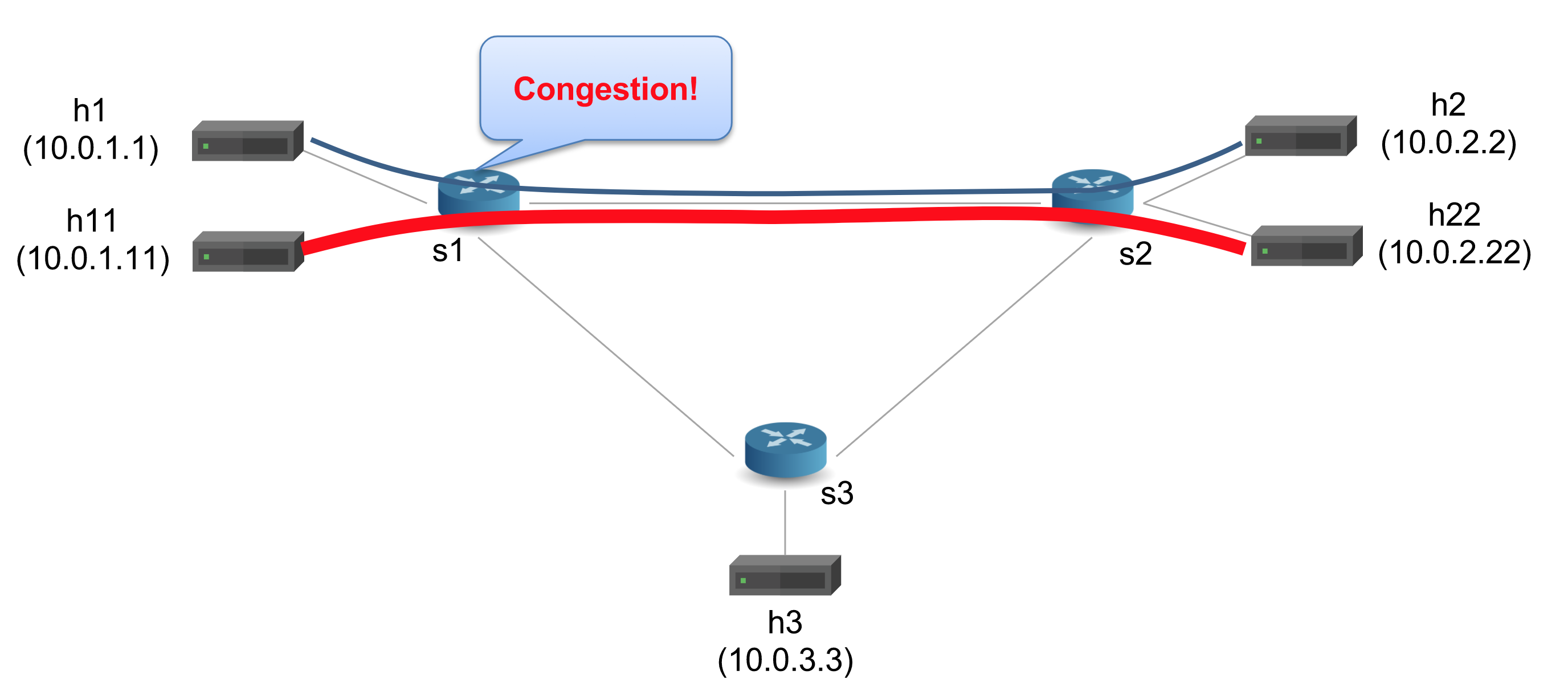
ecn.p4, and - start a Mininet instance with three switches (
s1,s2,s3) configured in a triangle. There are 5 hosts.h1andh11are connected tos1.h2andh22are connected tos2andh3is connected tos3. - The hosts are assigned IPs of
10.0.1.1,10.0.2.2, etc (10.0.<Switchid>.<hostID>). - The control plane programs the P4 tables in each switch based on
sx-runtime.json
- compile
-
We want to send a low rate traffic from
h1toh2and a high rate iperf traffic fromh11toh22. The link betweens1ands2is common between the flows and is a bottleneck because we reduced its bandwidth to 512kbps in topology.json. Therefore, if we capture packets ath2, we should see the right ECN value.
- You should now see a Mininet command prompt. Open four terminals
for
h1,h11,h2,h22, respectively:mininet> xterm h1 h11 h2 h22 - In
h2's XTerm, start the server that captures packets:./receive.py - in
h22's XTerm, start the iperf UDP server:iperf -s -u - In
h1's XTerm, send one packet per second toh2using send.py say for 30 seconds:
The message "P4 is cool" should be received in./send.py 10.0.2.2 "P4 is cool" 30h2's xterm, - In
h11's XTerm, start iperf client sending for 15 secondsiperf -c 10.0.2.22 -t 15 -u - At
h2, theipv4.tosfield (DiffServ+ECN) is always 1 - type
exitto close each XTerm window
Your job is to extend the code in ecn.p4 to implement the ECN logic
for setting the ECN flag.
Step 2: Implement ECN
The ecn.p4 file contains a skeleton P4 program with key pieces of
logic replaced by TODO comments. These should guide your
implementation---replace each TODO with logic implementing the
missing piece.
First we have to change the ipv4_t header by splitting the TOS field into DiffServ and ECN fields. Remember to update the checksum block accordingly. Then, in the egress control block we must compare the queue length with ECN_THRESHOLD. If the queue length is larger than the threshold, the ECN flag will be set. Note that this logic should happen only if the end-host declared supporting ECN by setting the original ECN to 1 or 2.
A complete ecn.p4 will contain the following components:
- Header type definitions for Ethernet (
ethernet_t) and IPv4 (ipv4_t). - Parsers for Ethernet, IPv4,
- An action to drop a packet, using
mark_to_drop(). - An action (called
ipv4_forward), which will:- Set the egress port for the next hop.
- Update the ethernet destination address with the address of the next hop.
- Update the ethernet source address with the address of the switch.
- Decrement the TTL.
- An egress control block that checks the ECN and
standard_metadata.enq_qdepthand sets the ipv4.ecn. - A deparser that selects the order in which fields inserted into the outgoing packet.
- A
packageinstantiation supplied with the parser, control, checksum verification and recomputation and deparser.
Step 3: Run your solution
Follow the instructions from Step 1. This time, when your message from
h1 is delivered to h2, you should see tos values change from 1
to 3 as the queue builds up. tos may change back to 1 when iperf
finishes and the queue depletes.
To easily track the tos values you may want to redirect the output
of h2 to a file by running the following for h2
./receive.py > h2.log
and just print the tos values grep tos h2.log in a separate window
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x3
tos = 0x3
tos = 0x3
tos = 0x3
tos = 0x3
tos = 0x3
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
tos = 0x1
Food for thought
How can we let the user configure the threshold?
Troubleshooting
There are several ways that problems might manifest:
ecn.p4fails to compile. In this case,makewill report the error emitted from the compiler and stop.ecn.p4compiles but does not support the control plane rules in thesX-runtime.jsonfiles thatmaketries to install using a Python controller. In this case,makewill log the controller output in thelogsdirectory. Use these error messages to fix yourecn.p4implementation.ecn.p4compiles, and the control plane rules are installed, but the switch does not process packets in the desired way. The/tmp/p4s.<switch-name>.logfiles contain trace messages describing how each switch processes each packet. The output is detailed and can help pinpoint logic errors in your implementation. Thebuild/<switch-name>-<interface-name>.pcapalso contains the pcap of packets on each interface. Usetcpdump -r <filename> -xxxto print the hexdump of the packets.ecn.p4compiles and all rules are installed. Packets go through and the logs show that the queue length was not high enough to set the ECN bit. Then either lower the threshold in the p4 code or reduce the link bandwidth intopology.json
Cleaning up Mininet
In the latter two cases above, make may leave a Mininet instance
running in the background. Use the following command to clean up
these instances:
make stop