* Updated the utils/run_exercise.py to allow exercises to customize host configuration from the topology.json file. Now hosts and `ping` each other in the basic exercise. Other Linux utilities should work as well (e.g. iperf). ``` mininet> h1 ping h2 PING 10.0.2.2 (10.0.2.2) 56(84) bytes of data. 64 bytes from 10.0.2.2: icmp_seq=1 ttl=62 time=3.11 ms 64 bytes from 10.0.2.2: icmp_seq=2 ttl=62 time=2.34 ms 64 bytes from 10.0.2.2: icmp_seq=3 ttl=62 time=2.15 ms ^C --- 10.0.2.2 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 2.153/2.540/3.118/0.416 ms mininet> pingall *** Ping: testing ping reachability h1 -> h2 h3 h2 -> h1 h3 h3 -> h1 h2 *** Results: 0% dropped (6/6 received) ``` Only updated basic exercise, still need to update other exercises. Also, updated the root-bootstrap.sh because I was running into issues with latest version of vagrant. * Accidentially added the solution to the basic exercise in the previous commit. Undoing that here ... * Updated the topology.json file and table entries for the basic_tunnel exercise. * Updated P4Runtime exercise with new topology and table entries. * Fixed MAC addresses in P4Runtime exercise. It is working now. * Fixed MAC addresses in P4Runtime exercise starter code * Updated ECN exercise to use new topology.json file. Updated the table entries / MAC addresses as well. * Updated the topology.json file and table entries for the MRI exercise. * Updated source_routing exercise with new topology file and verified correct functionality. * Updated load_balance exercise with new topology. * Moved basic exercise triangle topology into a separate folder * Added new topology for the basic exercise: a single pod of a fat-tree. * Updated Makefiles and run_exercise.py to allow exercises to configure each switch with a different P4 program. This is mainly for the firewall exercise. * Updated Makefiles of project to work with new utils/Makefile * Updated load_balance and p4runtime exercise Makefiles * Initial commit of the firewall exercise, which is a simple stateful firewall that uses a bloom filter. Need to update README files * Initial commit of the path_monitor exercise. It is working but still need to update the README and figure out what we want the tutorial attendees to implement. * Updated README file in firewall exercise. Also removed the bits from the starter code that we want the tutorial attendees to implement * Renamed path_monitor exercise to link_monitor * Updated the README in the link_monitor exercise and removed the bits from the starter code that we want the tutorial attendees to implement. * Updated README for the firewall exercise * Adding pod-topo.png image to basic exercise * Added firewall-topo.png image to firewall exercise * Added link-monitor-topo.png to link_monitor exercise * Updated README files to point to topology images * Updated top-level README to point to new exercises. * Fixed link for VM dependencies script in README * Updated bmv2/pi/p4c commits * Updated README files for exercises to fix some typos and added a note about the V1Model architecture. * Added a note about food for thought in the link_monitor README * Updated the firewall.p4 program to use two register arrays rather than a single one. This is to make the design more portable to high line rate devices which can only support a single access to each register array. * Minor fix to firewall exercise to get rid of compiler warning. * Updated comment in firewall exercise. * Minor (typo) fixes in the firewall ReadMe * More info in firewall exercise ReadMe step 2 * Updated firewall.p4 to reuse direction variable * More testing steps, small fixes in firewall exercise Readme * Added food for thought to firewall Readme * Cosmetic fixes to firewall ReadMe * Made a few updates to the basic exercise README and added more details to the link_monitor exercise README. Also added a command to install grip when provisioning the VM. This could be useful for rendering the markdown README files offline. * Updated top level README so it can be merged into the master branch. * Moved cmd to install grip from root-bootstrap to user-bootstrap
Implementing Basic Tunneling
Introduction
In this exercise, we will add support for a basic tunneling protocol to the IP router that you completed in the previous assignment. The basic switch forwards based on the destination IP address. Your jobs is to define a new header type to encapsulate the IP packet and modify the switch code, so that it instead decides the destination port using a new tunnel header.
The new header type will contain a protocol ID, which indicates the type of packet being encapsulated, along with a destination ID to be used for routing.
Spoiler alert: There is a reference solution in the
solutionsub-directory. Feel free to compare your implementation to the reference.
The starter code for this assignment is in a file called basic_tunnel.p4 and
is simply the solution to the IP router from the previous exercise.
A note about the control plane
A P4 program defines a packet-processing pipeline, but the rules within each table are inserted by the control plane. When a rule matches a packet, its action is invoked with parameters supplied by the control plane as part of the rule.
For this exercise, we have already added the necessary static control plane
entries. As part of bringing up the Mininet instance, the make run command
will install packet-processing rules in the tables of each switch. These are
defined in the sX-runtime.json files, where X corresponds to the switch
number.
Since the control plane tries to access the myTunnel_exact table, and that
table does not yet exist, the make run command will not work with the starter
code.
Important: We use P4Runtime to install the control plane rules. The content
of files sX-runtime.json refer to specific names of tables, keys, and
actions, as defined in the P4Info file produced by the compiler (look for the
file build/basic.p4info after executing make run). Any changes in the P4
program that add or rename tables, keys, or actions will need to be reflected
in these sX-runtime.json files.
Step 1: Implement Basic Tunneling
The basic_tunnel.p4 file contains an implementation of a basic IP router. It
also contains comments marked with TODO which indicate the functionality that
you need to implement. A complete implementation of the basic_tunnel.p4
switch will be able to forward based on the contents of a custom encapsulation
header as well as perform normal IP forwarding if the encapsulation header does
not exist in the packet.
Your job will be to do the following:
- NOTE: A new header type has been added called
myTunnel_tthat contains two 16-bit fields:proto_idanddst_id. - NOTE: The
myTunnel_theader has been added to theheadersstruct. - TODO: Update the parser to extract either the
myTunnelheader oripv4header based on theetherTypefield in the Ethernet header. The etherType corresponding to the myTunnel header is0x1212. The parser should also extract theipv4header after themyTunnelheader ifproto_id==TYPE_IPV4(i.e. 0x0800). - TODO: Define a new action called
myTunnel_forwardthat simply sets the egress port (i.e.egress_specfield of thestandard_metadatabus) to the port number provided by the control plane. - TODO: Define a new table called
myTunnel_exactthat perfoms an exact match on thedst_idfield of themyTunnelheader. This table should invoke either themyTunnel_forwardaction if the there is a match in the table and it should invoke thedropaction otherwise. - TODO: Update the
applystatement in theMyIngresscontrol block to apply your newly definedmyTunnel_exacttable if themyTunnelheader is valid. Otherwise, invoke theipv4_lpmtable if theipv4header is valid. - TODO: Update the deparser to emit the
ethernet, thenmyTunnel, thenipv4headers. Remember that the deparser will only emit a header if it is valid. A header's implicit validity bit is set by the parser upon extraction. So there is no need to check header validity here. - TODO: Add static rules for your newly defined table so that the switches
will forward correctly for each possible value of
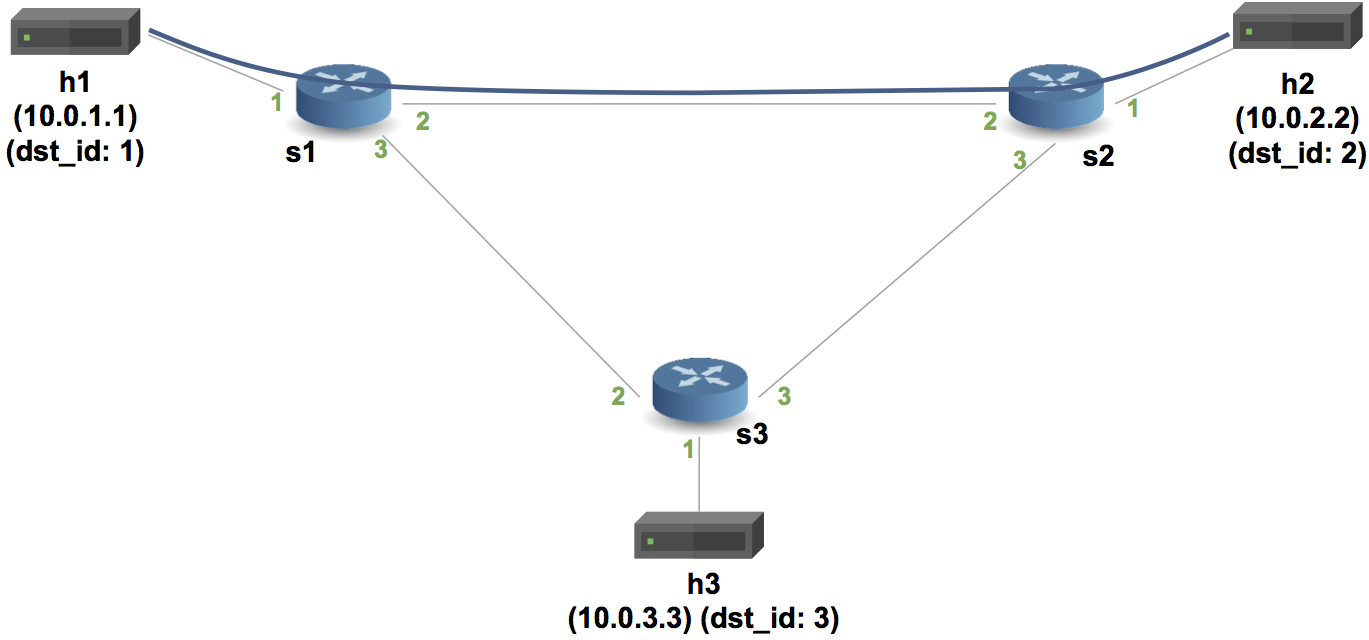
dst_id. See the diagram below for the topology's port configuration as well as how we will assign IDs to hosts. For this step you will need to add your forwarding rules to thesX-runtime.jsonfiles.
Step 2: Run your solution
-
In your shell, run:
make runThis will:
- compile
basic_tunnel.p4, and - start a Mininet instance with three switches (
s1,s2,s3) configured in a triangle, each connected to one host (h1,h2, andh3). - The hosts are assigned IPs of
10.0.1.1,10.0.2.2, and10.0.3.3.
- compile
-
You should now see a Mininet command prompt. Open two terminals for
h1andh2, respectively:
mininet> xterm h1 h2
- Each host includes a small Python-based messaging client and server. In
h2's xterm, start the server:
./receive.py
- First we will test without tunneling. In
h1's xterm, send a message toh2:
./send.py 10.0.2.2 "P4 is cool"
The packet should be received at h2. If you examine the received packet
you should see that is consists of an Ethernet header, an IP header, a TCP
header, and the message. If you change the destination IP address (e.g. try
to send to 10.0.3.3) then the message should not be received by h2, and
will instead be received by h3.
5. Now we test with tunneling. In h1's xterm, send a message to h2:
./send.py 10.0.2.2 "P4 is cool" --dst_id 2
The packet should be received at h2. If you examine the received packet you
should see that is consists of an Ethernet header, a tunnel header, an IP header,
a TCP header, and the message.
6. In h1's xterm, send a message:
./send.py 10.0.3.3 "P4 is cool" --dst_id 2
The packet should be received at h2, even though that IP address is the address
of h3. This is because the switch is no longer using the IP header for routing
when the MyTunnel header is in the packet.
7. Type exit or Ctrl-D to leave each xterm and the Mininet command line.
Python Scapy does not natively support the
myTunnelheader type so we have provided a file calledmyTunnel_header.pywhich adds support to Scapy for our new custom header. Feel free to inspect this file if you are interested in learning how to do this.
Food for thought
To make this tunneling exercise a bit more interesting (and realistic) how
might you change the P4 code to have the switches add the myTunnel header to
an IP packet upon ingress to the network and then remove the myTunnel header
as the packet leaves to the network to an end host?
Hints:
- The ingress switch will need to map the destination IP address to the
corresponding
dst_idfor themyTunnelheader. Also, remember to set the validity bit for themyTunnelheader so that it can be emitted by the deparser. - The egress switch will need to remove the
myTunnelheader from the packet after looking up the appropriate output port using thedst_idfield.
Troubleshooting
There are several problems that might manifest as you develop your program:
-
basic_tunnel.p4might fail to compile. In this case,make runwill report the error emitted from the compiler and halt. -
basic_tunnel.p4might compile but fail to support the control plane rules in thesX-runtime.jsonfiles thatmake runtries to install using the P4Runtime. In this case,make runwill report errors if control plane rules cannot be installed. Use these error messages to fix yourbasic_tunnel.p4implementation or forwarding rules. -
basic_tunnel.p4might compile, and the control plane rules might be installed, but the switch might not process packets in the desired way. The/tmp/p4s.<switch-name>.logfiles contain detailed logs that describing how each switch processes each packet. The output is detailed and can help pinpoint logic errors in your implementation.
Cleaning up Mininet
In the latter two cases above, make may leave a Mininet instance running in
the background. Use the following command to clean up these instances:
make stop
Next Steps
Congratulations, your implementation works! Move onto the next assignment p4runtime!